JMU Releases Dataminr Surveillance Records, Deactivates Account
James Madison University deactivates account with surveillance company Dataminr after a year-long relationship.
A month ago, I reported on the Virginia State Police’s “over $1,000,000” cost estimate to fulfill my FOIA request on records from surveillance company Dataminr. I further reported that, based on Virginia’s eProcurement Marketplace, James Madison University had purchased a single Dataminr user license, good from April 3, 2024 until April 2, 2025, for $10,000.
VSP: "Over $1,000,000" for Dataminr Surveillance Records
Last month, I read Sam Biddle’s article “LAPD Surveilled Gaza Protests Using This Social Media Tool” in The Intercept and, after learning about the use of Dataminr to surveil peaceful protests, wondered if it’s used by the government in Virginia. After all, as I reported in 2023, local law enforcement, the Virginia State Police (VSP), and even the FBI h…
Curious as to why a university would hire such a firm, I sent a FOIA request to JMU on April 24, 2025 for “all documents and communications received from any employee, representative, or account associated with the company Dataminr, Inc. from March 1, 2025 until today.”
After some back-and-forth, on May 5, 2025, JMU released the following files at no cost to me and without redactions. You can download them here:
Anatomy of a Dataminr “First Alert”
Of the 156 Dataminr “First Alert” emails to JMU Threat Assessment Analyst Dr. Wendy Rippon from March 1, 2025 until April 24, 2025, only one was even remotely related to James Madison University or the surrounding community. The vast majority dealt with international events, domestic politics, President Trump, and bomb threats outside of Virginia.
Let’s examine that single First Alert which concerns Harrisonburg, then look at one of the many bomb threat alerts, and finally examine a typical First Alert dealing with international politics.
As you can see below, the “First Alert | Urgent” emails provide links to media concerning topics that the user has previously selected via the “list” and “topic” functions referenced at the end of the email.
In the case of the alert below, it’s linking to a report on X about a structure fire in Harrisonburg. Although it’s an “urgent” alert, the email apparently arrived four hours after the X post.
Many of the alerts in the “First Alert Urgent Combined.pdf” file concern bomb threats, as they’re generated via the “USA-EDU Bomb Threats” list. Here’s one of them:
And here’s an example of one of the alerts devoted to international affairs, many of which (like the one below) also utilized ReGenAI to summarize previous updates:
JMU Deactivates Account
Granted, these records only span a mere month and a half of the year-long Dataminr license JMU held. But based on the images above, which are representative of the 156 pages of alerts turned over in response to my FOIA request, Dataminr alerts appear entirely irrelevant to JMU or public safety in Harrisonburg.
It’s not yet clear to me how Dataminr chooses which news sources and stories to distribute based on user-chosen lists, and I suspect many users, like myself, see these alerts more as spam than potentially useful.
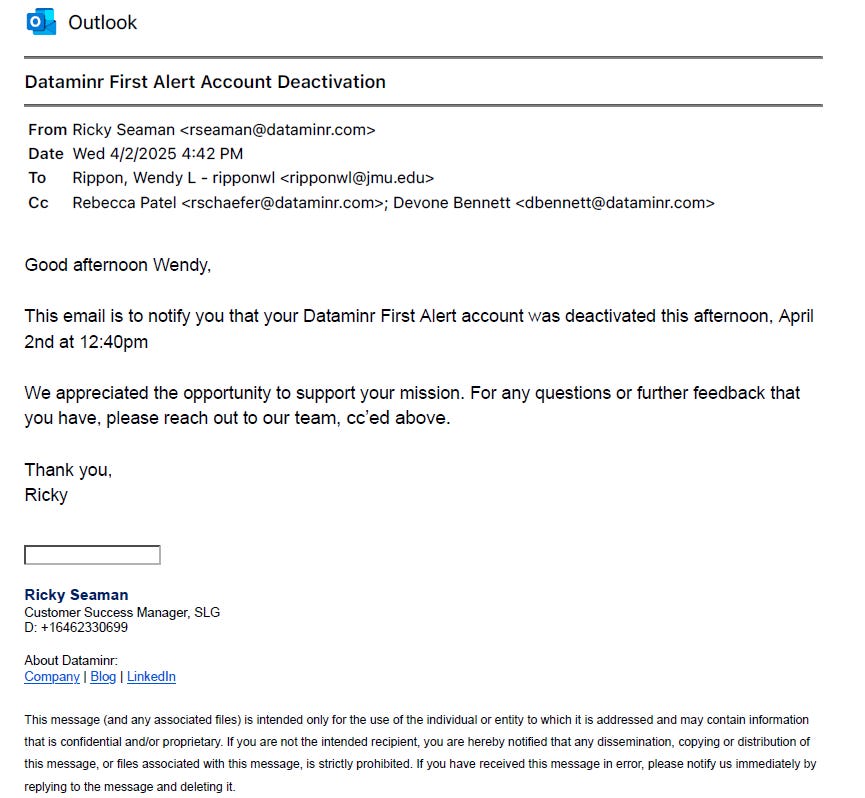
Although the FOIA records don’t explain why, they do show that JMU’s Dataminr First Alert account was deactivated on April 2, 2025 at 12:40pm:
The released records also show Dataminr Account Executive Devone Bennett contacting JMU Police Chief Anthony Matos in February and March, as the license renewal approached:
Right now, Virginia’s eProcurement Marketplace doesn’t show any current contracts between Dataminr and JMU. So Bennett’s efforts to sell a different product, “high-level, real-time emails focused on public safety events in and around the study abroad locations for JMU,” don’t appear to have been successful.
And, unlike last year, JMU apparently won’t be shelling out $10,000 per license on “First Alert” email blasts anymore.









Thank you for following up on the Dataminr story. On the one hand it's a comfort to know JMU wasn't actively surveilling students' social media through the account. On the other hand I question the judgment of a university spending $10,000 for essentially a whole lot of spam emails, WOW.